By Madhusudan Joshi
Push for linked, autonomous, shared and electrical (CASE) applied sciences have drastically elevated the digital content material within the automobiles. On a mean a typical trendy automotive has 50-plus Digital Management Models (ECUs), 100-plus microprocessors and greater than 100 million traces of software program code. These numbers are larger than in an plane, satellite tv for pc or rover. By growing electronics, digitization, and web connectivity, cars have joined the digital bandwagon and have grow to be weak to cyberattacks. Connectivity, large knowledge acquisition, large knowledge evaluation with the assistance of synthetic intelligence (AI) and social engineering have made your complete automotive ecosystem part of the IoT community.
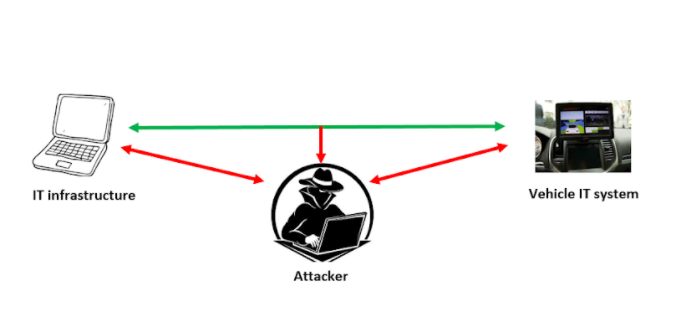
The idea of cyber safety turns into extra related within the automotive context because the methods and subsystems associated to security of car customers shall be protected towards unauthorized entry, malfunction and many others. Along with security, danger of economic influence can be concerned in an enormous means. These days automobiles are linked to a number of IT gadgets like cellphones, computer systems, Wi-Fi routers, and different automobiles. Therefore there’s at all times a danger of private knowledge/data being misused by the black-hat hackers.
A hacker can intrude with the automobile security methods or steal delicate data. The cyber-attacks should not confined to the automobile degree however can transcend to the back-end or the third-party servers. At instances, moral hackers and researchers have demonstrated circumstances of cyber-attacks on the automobiles.
Ransomware in parking tons, controlling home EV charging by accessing Wi-Fi, controlling automotive infotainment, braking, engine cut-off, local weather management and hacking the keyless management system are examples for cyber-attacks on automobiles.
Innovation and cyber threats
Each automotive innovation associated to data know-how, digitization, IoT and many others. is a possible gateway for cyber-attacks. Following are the examples of improvements within the CASE know-how automobiles:
- Related and shared automobiles: Bluetooth, Wi-Fi, vehicle-to-vehicle, vehicle-to-infrastructure, vehicle-to-cloud, vehicle-to-everything.
- Electrical automobiles: charging networks.
- Autonomous automobiles: sensors and knowledge will be manipulated to regulate the automobile.
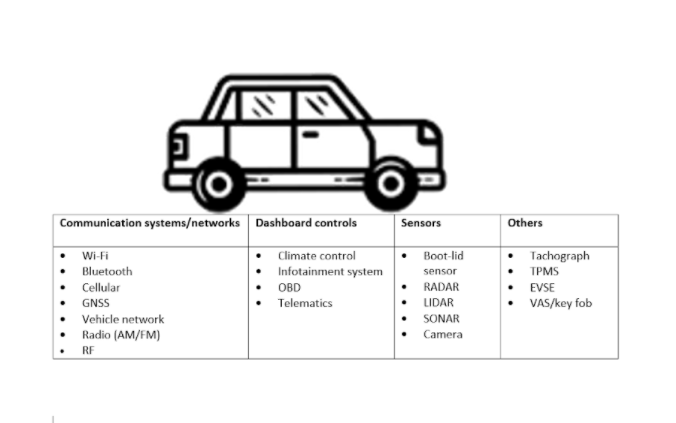
With a view to preserve automobiles protected from numerous cyber threats, it’s crucial that the proper cybersecurity measures are at all times in place. For that it’s mandatory to grasp the form of threats that may have an effect on a automobile. Some frequent cyber-attacks related to automotives are as beneath:
1.Malware: It consists of various kinds of assaults like virus, Trojans, worms, ransomware, spyware and adware and many others. Malware typically breaches the integrity of a community when a person installs a ‘planted’ hyperlink that’s supposed to put in a malicious software program contained in the system. Malware as soon as put in can deny the entry to the system to the licensed customers, steal confidential data, disrupt the system or make it inoperable. For instance, a virus assault on ABS ECU can disrupt the braking system of the automobile.
2.Man-in-the-middle assault: On this case, thehacker forcefully inserts himself between the consumer and the server intercepting a two-party transaction. In such an assault, the attacker steals or manipulates the info. Such assaults are tough usually to detect. In case of automobiles, as an example, such assaults will be brought about whereas utilizing an unsecured Wi-Fi connection.
3.Web-of-things (IoT) assaults: Web connectivity of issues supplies a gateway to the attackers to breach and exploit different gadgets within the community. Growing IoT gadgets in automobiles is a matter of nice concern on this regard.
4.Password assault: On this case, the attackers might use myriads of strategies to decipher a non-public password of a person. That is finished utilizing social media platforms, accessing the password database, exploiting networks to acquire unprotected passwords, or by hit and trial (brute-force assault). Automotive infotainment methods could also be generally attacked on this means.
5.Denial-of-service (DoS) assaults: Such assaults are supposed to saturate the system sources thereby impeding the response. Consequently, the system is overloaded and fails to course of a official request. As an illustration, such an assault on the local weather management ECU of a automotive could make the driving force helpless.
6.Command injection knowledge corruption: Attackers on this case inject a command to an ECU to achieve entry and corrupt the saved knowledge. Relying on the criticality of the ECU, such assaults can have critical implications for a automobile system.
Automotive cybersecurity strategy
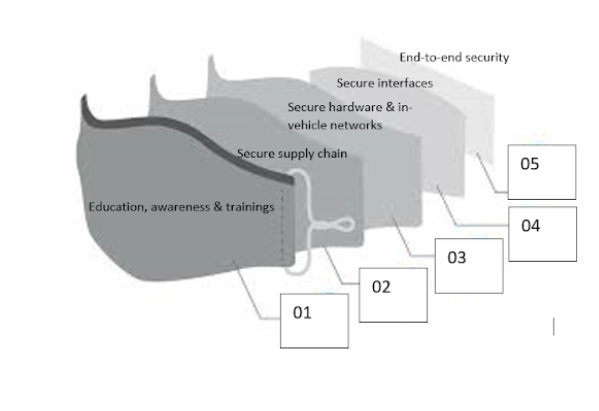
The topic of automotive cybersecurity must be handled in a complete method. This consists of information base enhancement, improvement of enabling instruments, establishing regulatory framework and introduction of business greatest practices (danger evaluation and administration, consciousness and coaching, risk detection, monitoring and evaluation and many others.). It’s endorsed to safe the potential gateways for cyberattacks in a automobile atmosphere. This may be achieved by hardening the automobile digital structure and a multilayered strategy is usually recommended for a similar. That is often achieved by means of encryption, real-time system monitoring, fast incident response towards any try of unauthorized entry and closed-loop suggestions mechanism. Completely different facets like V2X communication, firmware updates, intrusion detection and many others. shall be addressed whereas approaching automotive cybersecurity.
Briefly, It’s pertinent to present due consideration to the privateness and cybersecurity all through the life cycle of the automobile ranging from idea to end-of-life in view of security of the automobile customers.
There are quite a few methods to enhance cybersecurity within the automotive atmosphere. Some apparent safety strategies embody managed entry to the debugging and diagnostic ports, by introducing sturdy & dynamic password administration system, tight management over automobile diagnostic instrument entry, extremely safe entry to firmware, safe entry to automobile communication methods, isolation of car structure, managed entry to the community ports, automobile protocols, back-end servers, wi-fi interfaces and many others. Whereas guaranteeing the cybersecurity safety for a automobile, it is very important remember the side of serviceability. Whereas controlling the unauthorized entry to make sure safety towards cybercrimes, undue restrictions shall not be imposed on the licensed third-party providers like restore, upkeep and many others.
Automotive cybersecurity duty matrix
Cybersecurity throughout the automotive worth chain begins from the OEM that has the duty to craft a safe automobile structure. Whereas procuring the components, methods and subsystems from Tier-1 or aftermarket, clear tips shall be laid down across the cybersecurity rules like ISO/SAE DIS 21434. Tier-1 suppliers should be effectively conscious of the cyber dangers hooked up to the components being equipped to OEMs. As an illustration, the ABS system provider shall conform to the event course of in view of the cyber-risks contemplating {hardware} and software program ranges. Tier-1 suppliers typically outsource know-how options to the engineering service suppliers for design, improvement, proto typing, testing, validation, configuration, integration, protocols and many others. Just like Tier-1 suppliers, engineering service suppliers shall meet all the necessities to mitigate cyber threats concerned associated to their providers and merchandise.
ISO/SAE 21434 customary overview
Automotive cybersecurity is primarily ruled by ISO/SAE DIS 21434 customary. The usual covers the engineering facets of cybersecurity for on-road automobiles. Revealed in 2016 and co-authored by ISO & SAE, the usual supplies tips to handle cybersecurity within the automotive area. ISO/SAE DIS 21434 consists of the scope & definitions; Targets, methods, & goals of cybersecurity administration; Strategies for danger evaluation; Menace evaluation and defines Cybersecurity Assurance Ranges (CALs).
Conclusion
Cybersecurity is a topic of paramount significance for automotive OEMs and different stakeholders. It additionally has profound implications on the automobile high quality as automobiles these days are part of the IoT community. It’s evident that challenges linked to cybersecurity administration would preserve your complete automotive fraternity busy for the following decade or so. All completely different aspects of automotive cybersecurity together with computing methods, communication methods, automobile interfaces, knowledge switch, again finish, cloud and many others. shall be touched upon to have a protected and safe automotive ecosystem. This may be achieved by making your complete worth chain associated to the automotive improvement (from idea part to end-of-life) end-to-end safe in-line with relevant rules, tips and business greatest practices.
(Disclaimer: Madhusudan Joshi is Head-E&E, ICAT-Manesar. Views are private.)
Additionally Learn: